Blog
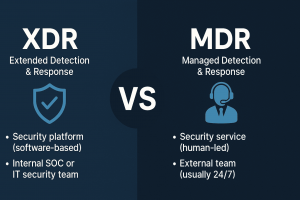
What Is the Difference Between XDR and MDR in Cybersecurity?
XDR is a security platform unifying threat data for automated response, while MDR is a managed service with human
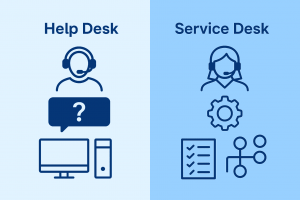
Helpdesk vs Service Desk: What’s the Difference for SMB IT Support?
Helpdesks fix day-to-day IT issues fast; service desks manage IT at a business level. SMBs must choose based on
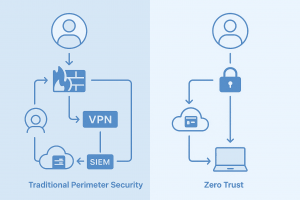
Zero Trust vs Traditional Perimeter Security: Which Protects SMBs Better?
Cybersecurity is no longer a technical afterthought. It’s now a strategic necessity, especially for small to midsize businesses (SMBs).
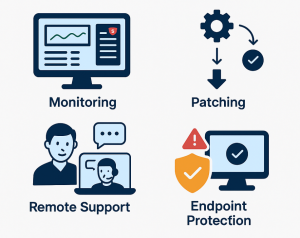
What Is an RMM Tool? Benefits for Managed IT Support Providers
Managed IT providers are expected to deliver fast, reliable, and proactive support, often without setting foot in the client’s
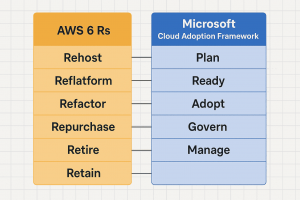
AWS 6 Rs Framework vs Microsoft Cloud Adoption Framework: Strategic Comparison for Cloud Migration Leaders
Choosing the Right Cloud Migration Framework: Strategy First, Tools Second Migrating to the cloud is no longer a technical
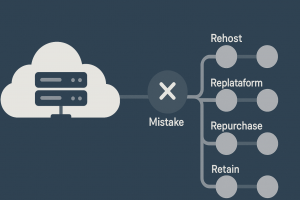
Common Mistakes Businesses Make When Applying the 6 Rs of Cloud Migration
The 6 Rs of cloud migration—Rehost, Replatform, Refactor, Repurchase, Retire, and Retain—form a strategic framework that helps organizations decide
How to Choose the Right Cloud Migration Strategy for Your Business
Choosing the right cloud migration strategy is a critical decision that determines the stability, scalability, and cost-efficiency of your
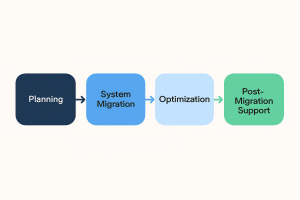
End-to-End Cloud Migration Solutions Explained: The Full Lifecycle for Business-Ready Cloud Transformation
Moving business systems to the cloud is not a matter of uploading data. It is a full-scale transformation of
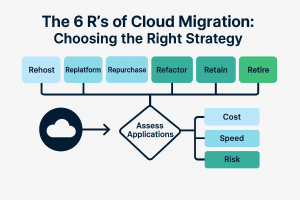
The 6 Rs of Cloud Migration Strategy: Framework, Use Cases, and Deployment Models
Modern organizations no longer view cloud adoption as optional. The question is not whether to migrate, but how to
Business-Optimized Cloud Computing Solutions
How CitySource Helps You Stop Managing Infrastructure—and Start Running a Smarter Business Why Businesses Are Moving to the Cloud—But
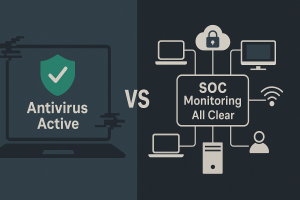
5 Cyber Threats Your Antivirus Misses (and How Our SOC Detects Them)
Why Antivirus Alone Leaves Security Gaps Antivirus software plays an important role in protecting individual devices by detecting and

What Happens Inside a Real Security Operations Center (SOC)?
A Security Operations Center (SOC) isn’t just a technical support room. It’s the brain of an organization’s entire cybersecurity
